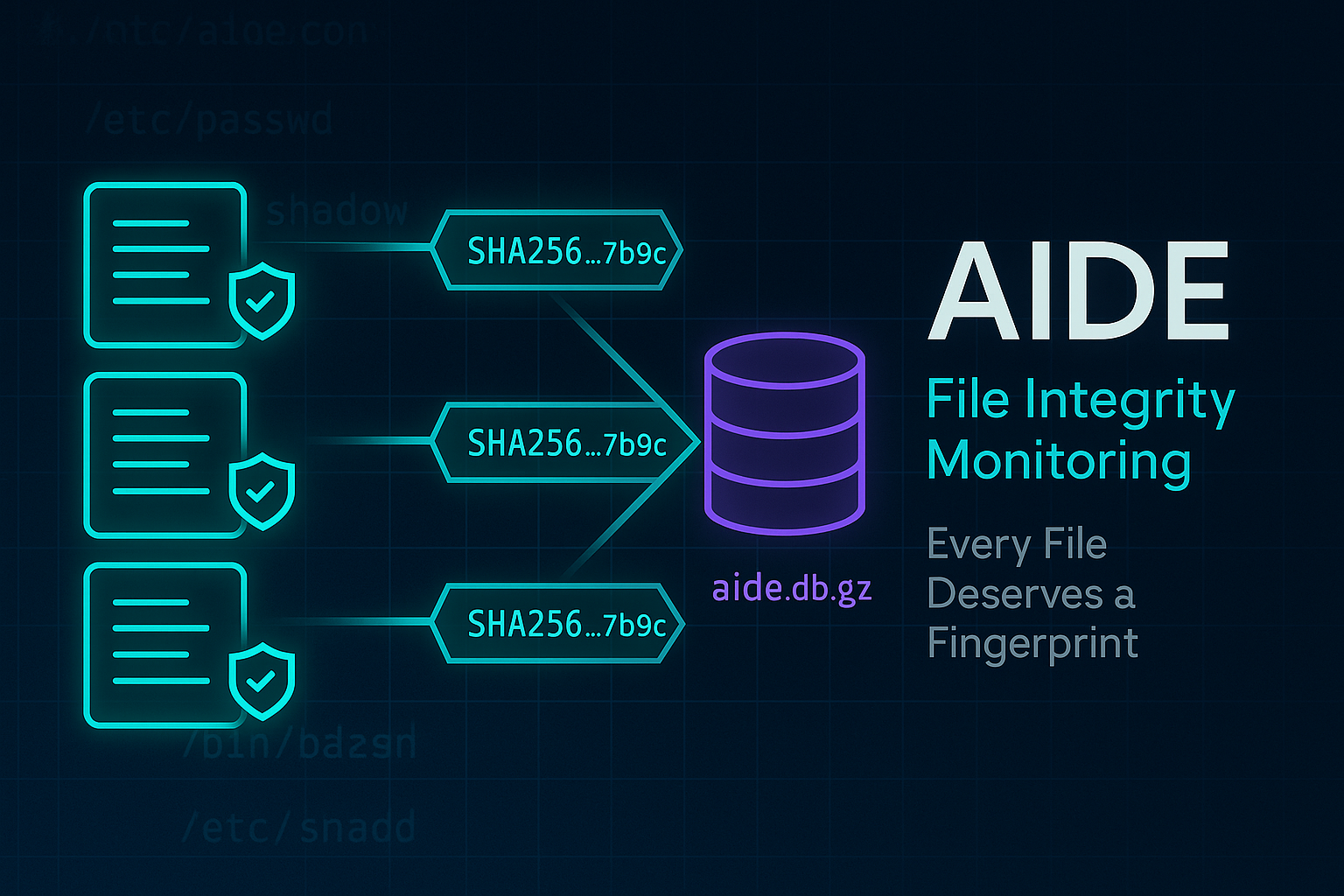
AIDE - File Integrity Monitoring for System Security
Before dashboards, before SIEMs, there was one simple question: “Did my files change?” AIDE still answers that — silently and faithfully. 🔍 Why File Integrity Still Matters My first exposure t...

Before dashboards, before SIEMs, there was one simple question: “Did my files change?” AIDE still answers that — silently and faithfully. 🔍 Why File Integrity Still Matters My first exposure t...
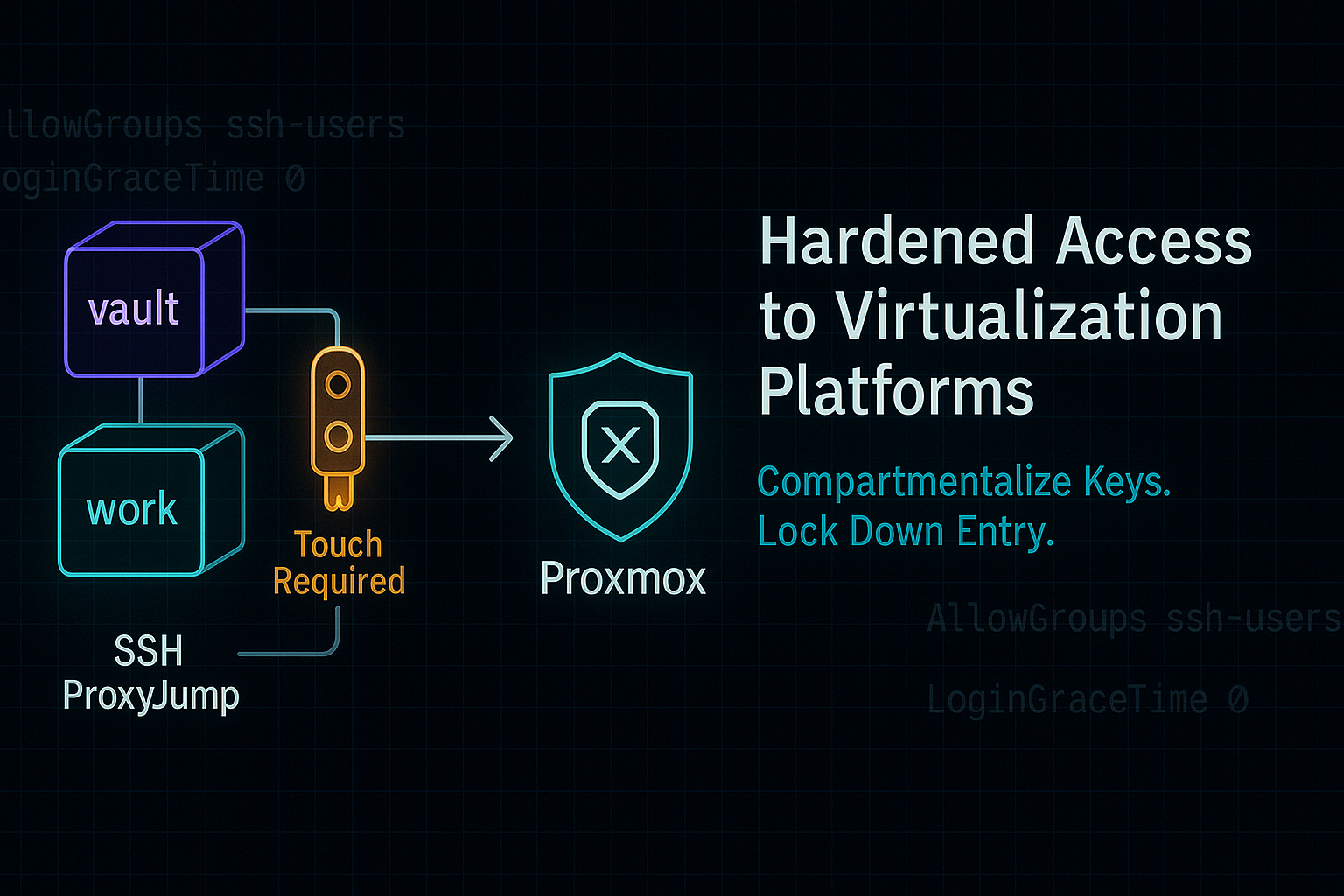
Virtualization tech — once locked away in enterprise data centers — now powers all kinds of home labs. I use mine for learning, tinkering, and running services like Proxmox VE. Whether you’re runni...
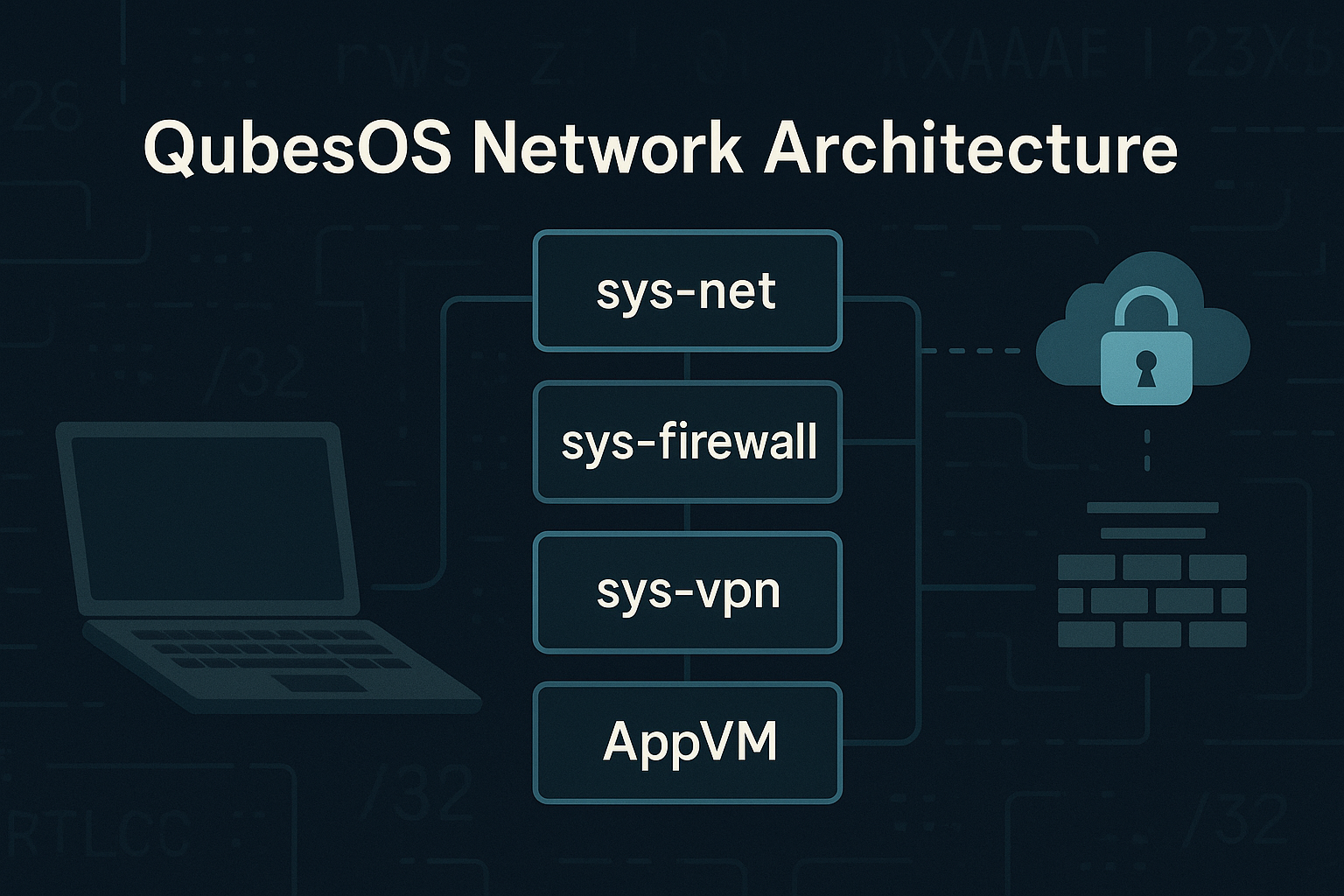
“A deep dive into QubesOS network isolation and how to verify your VPN, TOR, and inter-VM firewalling actually works.” 📝 Introduction I began my IT career as a client/server programmer before t...
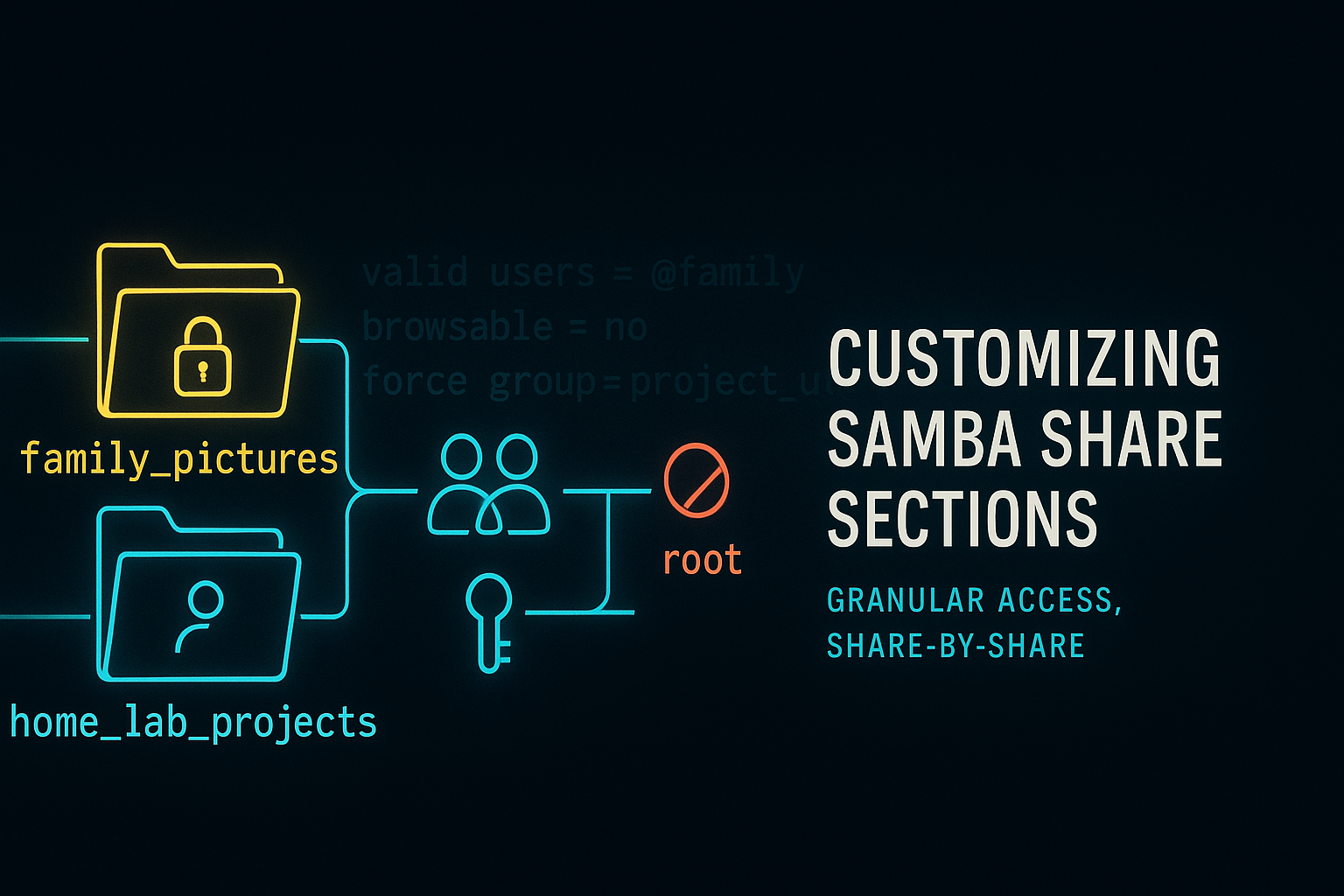
If you’re setting up Samba shares, you’re probably aiming for something deceptively simple—“I just want to share a folder.” But like many IT pros (myself included), you’ve likely hit a moment wher...

When I first got into IT, I was all about planning. I’d spend hours researching, mapping everything out, and building the “perfect” install plan before touching anything. But, like most people find...

Enable secure, controlled file sharing across Windows and Linux clients using Samba. This guide walks you through a basic setup, which forms the foundation for building a secure, maintainable file ...
🧰 Samba Admin Cheatsheet for Oracle Linux 9 Quick reference for troubleshooting, securing, and validating Samba shares on Oracle Linux 9. This cheatsheet complements the main setup guide, provi...

Making CUPS Classes Work for You “There’s never enough time to do it right, but there’s always enough time to do it over.” — Jack Bergman Time and again, I’ve been on projects where the origi...

Introduction: Shattering the Myth A few years ago, an IT professional I trusted made a statement that stuck with me: Linux is not secure. He didn’t mean Linux was worse than Windows or macOS, but ...

Introduction Running a desktop environment inside a hypervisor isn’t new. Tech enthusiasts and home lab users have been doing it for years with tools like VMware Workstation and VirtualBox. These ...