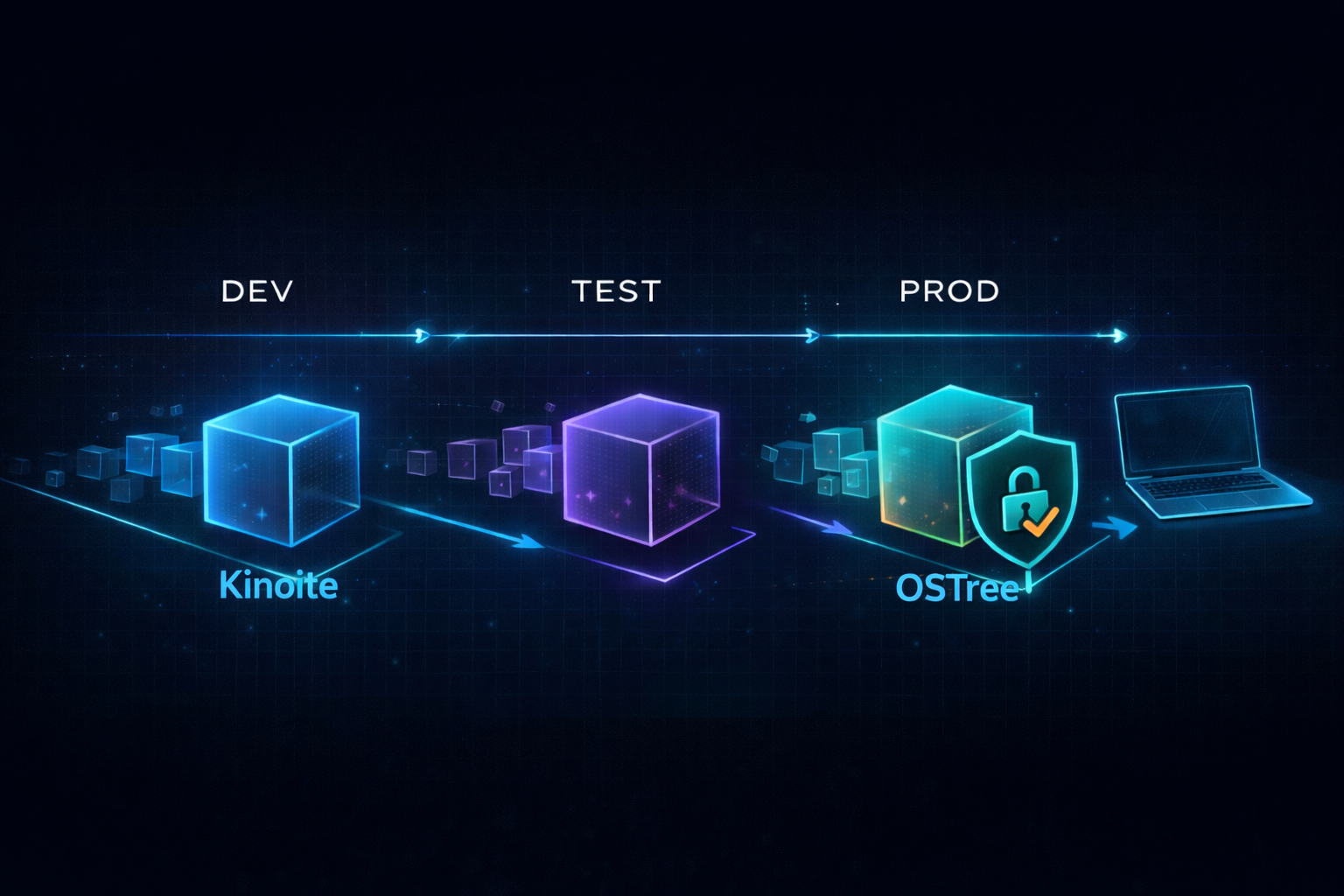
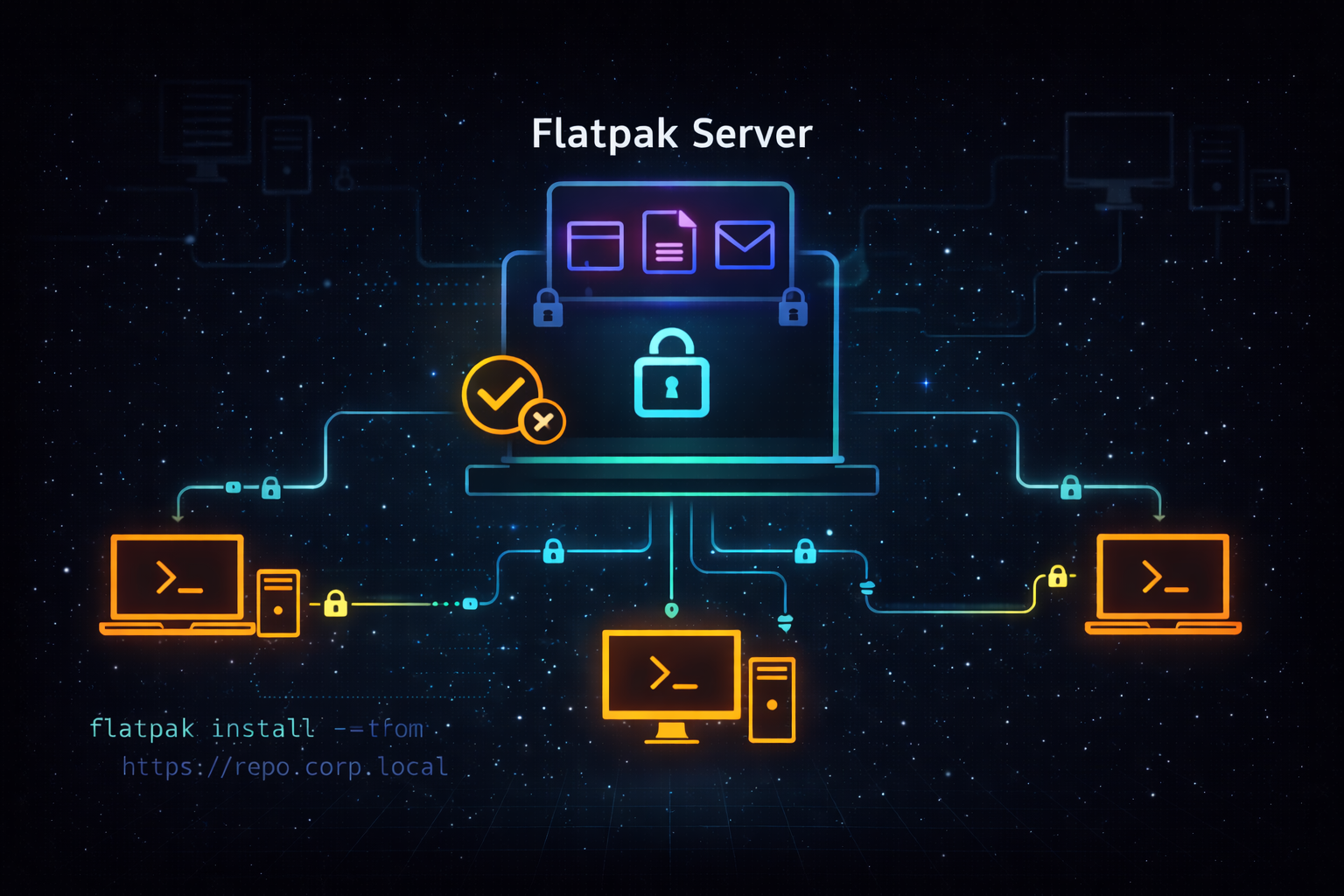
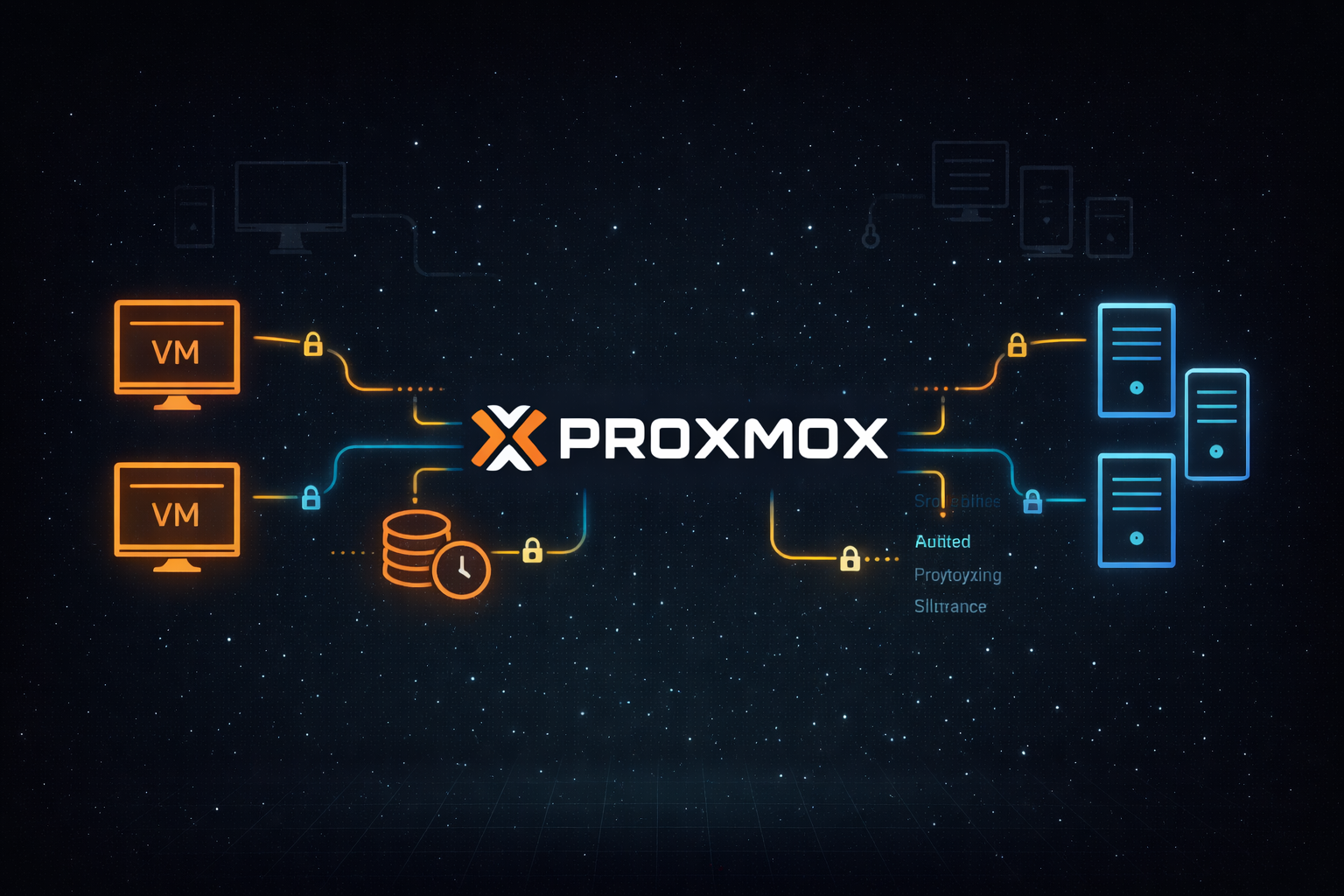
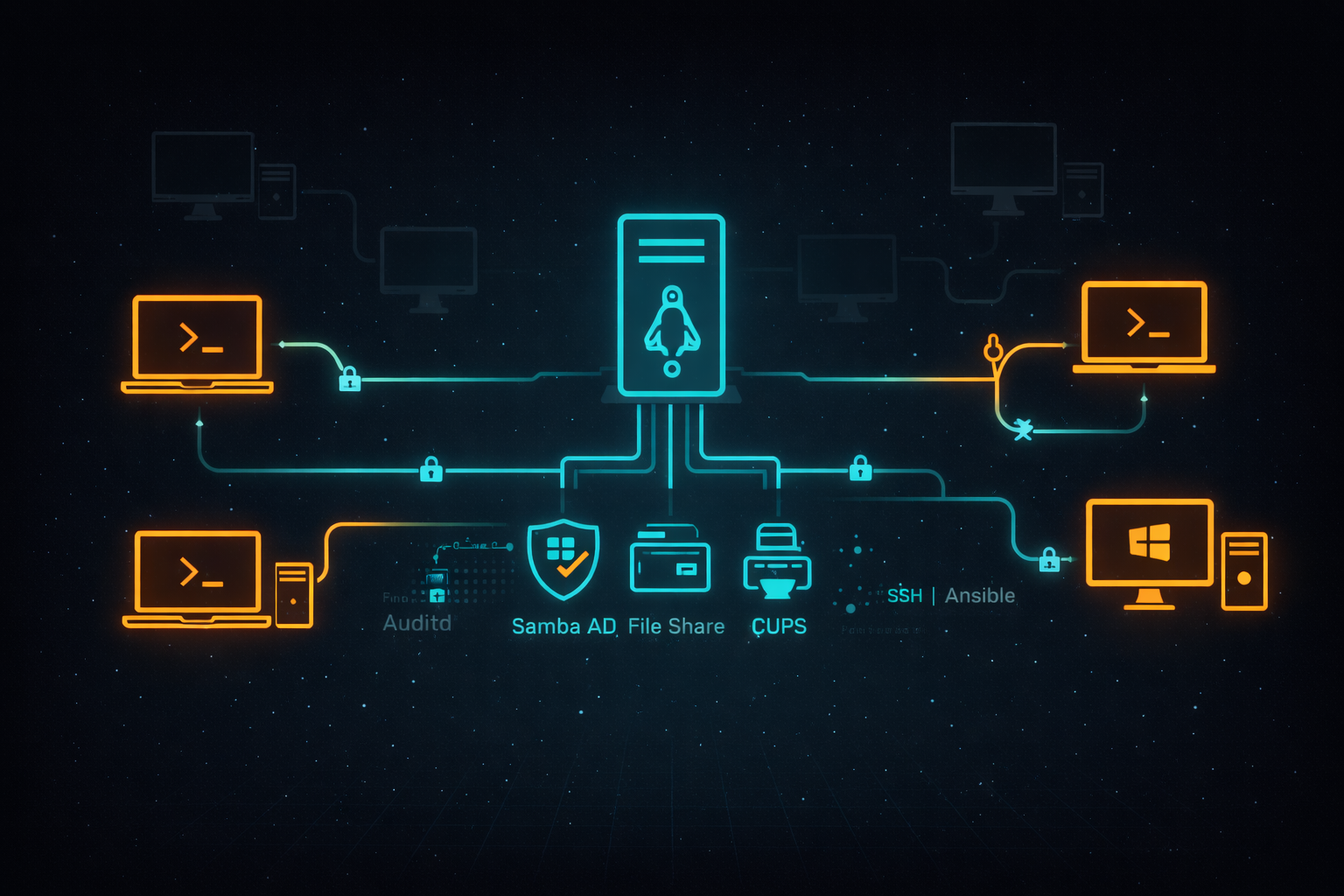
Understanding the Kinoite Stack: A Technology Primer
Introduction Modern enterprise desktop management leverages several specialized technologies that work together to create reliable, secure, and maintainable systems. This primer provides business-...